Email spam is inbox mail also referred to as junk email, spam mail or simply spam, unsolicited messages sent in bulk via email (spamming). The name comes from a Monty Python sketch in which the canned pork product name Spam is ubiquitous, inescapable and repetitive. Email spam has grown steadily since the early 1990s and was estimated to account for nearly 90% of total email traffic by 2014.
Since the cost of spam is mostly borne by the recipient, it is effectively advertising due to postage. This makes it an excellent example of a negative externality. The legal definition and status of spam varies from jurisdiction to jurisdiction, but nowhere have laws and cases been particularly successful in preventing spam.
Most email spam messages are commercial in nature. Commercial or not, many are not only annoying as a form of attention-stealing, but also dangerous because they may contain links to phishing web sites or sites that are hosting malware or include malware as file attachments. Spammers collect email addresses from chat rooms, websites, subscriber lists, newsgroups, and viruses that harvest users' address books. These collected email addresses are also sometimes sold to other spammers.
Spam is annoying, but it's also a threat. While many of us may think we are smart enough to recognize any form of this, spammers regularly update their methods and messages to trick potential victims. The reality is that we are all constantly under attack by cybercriminals and the proof is in your inbox.
So read the article to know what is spam, how to recognize it and how to protect yourself from it.
Definition of spam
Spam is any form of unsolicited, unsolicited digital communication sent in bulk. Spam is often sent via email, but it can also be delivered via text messages, phone calls, or social media.
What does spam mean?
Spam is not an acronym for computer threats, although some have been suggested (for example, stupid pointless annoying malware). The inspiration for the use of the word "spam" to describe widespread unsolicited messages is a Monty Python skit in which the actors declare that everyone has to eat spam, whether they like it or not. Likewise, everyone with an email address has to unfortunately be bothered by spam messages, whether we like it or not.
If you are interested in the source of the spam in more detail, see the spam history below
Types of Spam
Spammers use many forms of communication to send their unsolicited messages in bulk. Some of these marketing messages sell unsolicited products. Other types of spam messages can spread malware, trick you into revealing personal information, or scare you into paying to get out of trouble.
Email spam filters catch many of these types of messages, and phone carriers often warn you about the "spam risk" from unknown callers. Whether via email, text, phone, or social media, some spam messages come out, and you want to be able to recognize them and avoid these threats. Below are the different types of spam to spot.
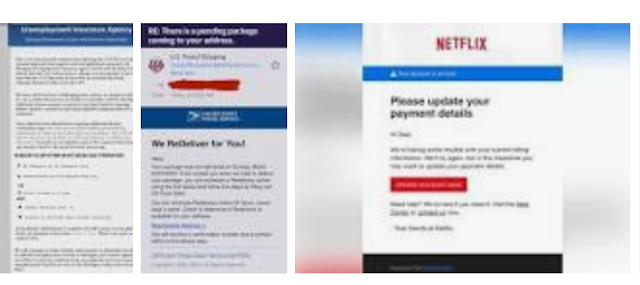
Phishing email
Phishing emails are a type of spam cybercriminals send to many people, hoping to "hook" some people. Phishing emails trick victims into giving up sensitive information like website logins or credit card information.
Adam Kuzawa, director of Malwarebytes Labs, said of phishing emails: “Phishing is the simplest form of cyber attack and, at the same time, the most dangerous and effective. Because it attacks the weakest and most powerful computer on the planet: the human mind."
Email spoofing
A spoofed email imitates, or spoofs, an email from a legitimate sender and asks you to take some action. Well-executed spoofs will have familiar branding and content, often from a large well-known company like PayPal or Apple. Common email spoofing spam messages include:
- A request for payment of an outstanding invoice
- A request to reset your password or verify your account
- Verification of purchases you have not made
- Request for updated billing information
Tech support scam
In a tech support scam, the spam message indicates that you have a technical problem and should contact tech support by calling the phone number or clicking a link in the message. Like email spoofing, this type of spam often claims to be from a major tech company like Microsoft or a cybersecurity company like Malwarebytes.
If you think you have a technical problem or malware on your computer, tablet or smartphone, you should always go to the official website of the company you want to call for tech support to find valid contact information. Remote tech support often involves remote access to your computer to help you, and you don't want to accidentally give that access to a tech support scammer.
Current events are scandals
News topics can be used in spam messages to get your attention. As the world faced the Covid-19 pandemic in 2020 and work from home increased, some scammers sent out spam messages promising remote jobs that paid in Bitcoin. In the same year, another popular spam topic was related to offering financial relief to small businesses, but the scammers ended up asking for bank account details. News headlines can be catchy, but beware of potential spam messages
Advance-fee scams
Anyone who has been using email since the 90s or 2000s is probably familiar with this type of spam. Sometimes called the "Nigerian Prince" email because it has been the purported sender for years, this type of spam promises a financial reward if you first pay a cash advance. The sender usually indicates that this cash advance is some kind of processing fee or earnest money to unlock a larger amount, but once you pay, they disappear. To make it more personal, in similar scams the sender pretends to be a family member who is in trouble and needs money, but if you pay, unfortunately the result is the same.
Malspam
Short for "malware spam" or "malicious spam," malspam is a spam message that delivers malware to your device. Unsuspecting readers who click on a link or open an email attachment end up with some form of malware, including ransomware, trojans, bots, data stealers, cryptominers, spyware, and keyloggers. A common distribution method is to include malicious scripts in known types of attachments, such as Word documents, PDF files, or PowerPoint presentations. Once the attachment is opened, the scripts run and retrieve the malware payload
Spam calls and spam texts
Have you ever received a robocall? This call is spam. A text message from an unknown sender prompting you to click on an unknown link? This is called text message spam or "smishing", a combination of SMS and phishing.
If you receive spam calls and texts on your Android or iPhone, most major carriers give you the option to report spam. Blocking numbers is another way to combat mobile spam. In the US, you can add your phone number to the National Do Not Call Registry to try to reduce the amount of unwanted sales calls you receive, but you should be wary of scammers who ignore the list.
How can I stop spam?
While it may not be possible to completely avoid spam, there are steps you can take to protect yourself from falling victim to scams or being phished by spam messages:
Learn fishing spots
We can all be victims of phishing attacks. We can be in a hurry and click on a malicious link without realizing it. If a new type of phishing attack comes along, we may not recognize it easily. To protect yourself, a spam message isn't just annoying—it's a phishing attempt—learn to check for some key signs:
- Sender's email address: If an email from a company is valid, the sender's email address matches the domain it claims to represent the company. Sometimes these are obvious, like example@abkljzr09348.biz, but other times the changes are less noticeable, like example@paypa1.com instead of paypal.com.
- Missing Personal Information: If you are a customer, the company should have your information and will probably address you by your first name. A missing personal greeting alone isn't enough to identify a phishing email, but it's one thing to look for, especially in messages that say they're from a company you do business with. Getting an email saying your account is locked or you owe money is worrying, and sometimes we rush to click a link to fix the problem. If it's phishing, that's exactly what the sender wants, so be careful and check whether the email is generic or specifically addressed to you.
- Links: Beware of all links with buttons in an email. If you receive a message from a company with which you have an account, it's a good idea to log into your account to see if there's a message, rather than clicking on the link in the message without verifying first. You can contact the company to find out if a suspicious message is legitimate or not. If you are in doubt about a message, do not click on any link.
- Grammatical errors: We all make them, but a company that sends a valid message probably won't have too many punctuation errors, poor grammar, and spelling mistakes. These can be another red flag to indicate that the email may be suspicious.
- Too-good-to-be-true offer: Many phishing messages pretend to be large, well-known companies, hoping to lure readers who do business with the company. Other phishing attempts offer something free, such as cash or a desired reward. The saying is often true that if something sounds too good to be true, it probably is, and this could be a warning that a spam message is trying to get something from you instead of giving you something.
- Attachments: Unless you expect an email with attachments, always be careful before opening or downloading them Using anti-malware software can help by scanning downloaded files for malware